For those just tuning in, Mike Lindell, the “Pillow Guy” is claiming that Biden is illegitimate. Specifically, that China hacked into the election systems and claims he can prove it.
On August 10th through 12th 2021 he is hosting a “Cyber Symposium” to evaluate said data and holding a hackathon, of sorts, where anyone who can prove the data is not really from the 2020 election is eligible for a five-million dollar award. For those interested you can see it live streamed here.
Before we get started, let me lay a few things out:
- I am entertaining these claims with an open mind (though I am doubtful)
- Only real question: “where would one get data to prove this?”
- Until we know where the data is coming from, one cannot determine the validity
- I have watched Lindell for tens of hours at this point, I believe he’s truly out to “do the right thing”
- I will not dismiss his claims out of hand, nor will I mock or ridicule. He makes serious claims, let’s see the validation
With that in mind, this article is attempting to identify his data source(s), evaluate if it’s possible to capture said data and is it likely that a hack occurred.
Where could the data come from?
Mike Lindell claims that he has all the packet captures from the election.
Packet Capture refers to the action of capturing Internet Protocol (IP) packets for review or analysis. The term can also be used to describe the files that packet capture tools output, which are often saved in the .pcap format. Capturing packets is a common troubleshooting technique for network administrators, and is also used to examine network traffic for security threats. (varonis.com/blog/packet-capture)
How might one capture these packets? There are only a few options:
- voting machines or servers (central logging location)
- source routers
- antivirus software
- content delivery network (CDN)
- internet backbone(s)
- Verizon, AT&T or other network provider
The question is who, what and where were these packets supposedly captured?
After researching, I am:
- 95% confident hacks on voting systems occurred
- 60% confident the hacks materially changed one or more state election
- 10% confident they have the packet captures proving the election was hacked
Honestly, I don’t believe Lindell knows where this data came from. Further, if the packet capture data is legitimate, I would guess it was from another group of hackers hacking or monitoring the election themselves (Russian, China, U.S. Gov, etc).
Only hand audits & re-canvasing are going to be able to prove the results Lindell claims, which perhaps is the point.
What Mike Lindell is Claiming
Skip The Propaganda
Personally, I think this section is immaterial to the actual discussion. However, because it was in the news and CNN just released propaganda around this topic, it must be discussed. The reality is they don’t review the data in detail and more importantly they don’t validate the data source. As such, it’s not worth listening to. However, if you’re interested feel free to dive in below.
MyPillow's CEO keeps pushing false claims about the 2020 election.
"No matter who says there was no widespread fraud in the election… Mike Lindell's conclusion is the same — they are all wrong," reports @DrewGriffinCNN. pic.twitter.com/NDHZY0BqL6
— Anderson Cooper 360° (@AC360) August 6, 2021
For those who watched the CNN clip, I think it’s important to Mike Lindell’s response to CNN.
Now that we got that out of the way, let’s get into the interesting part.
Absolute Proof
In Mike Lindell’s video Absolute Proof (aired Feb 5, 2021), Lindell presents some of his “proof” in an attempt to explain what he believes happened. The “proof” is packet information, containing both the routing information AND the data itself (implying a insecure connections). This enables tracking of data between the Dominion Voting machines (among others) to and from servers from around the U.S. and the world. There’s also clips of Dominion employees admitting their machines can connect to the internet (over cellular connections or LAN).
First, I think the video is worth watching in its entirety. Regardless of what you believe, there are tens of millions of people (if not hundreds of millions) that believe portions of what is presented. It’s important everyone is on the same page.
That being said, in regard to our investigation of “where did the routing data come from?” this video provides multiple pieces of the story (timestamps provided):
- 1:02:00 – Lindell speaks to “Patrick Colbeck“, former Michigan senator, Microsoft small business specialist and did cabling design on the space station. He was a poll challenger in Michigan on election night. He claims and explains how he believes the computers were networked (see video for details).
- 1:25:00 – They go over the dominion manual, and explains how to connect the dominion machines to the internet.
- 1:26:00 – “Eric Coomer” (Dominion Voting Systems in 2017) discussing the machines sending the data over mobile networks (Verizon, AT&T, etc)
- 1:36:00 – Lindell introduces “Mary Fanning” will come into the video and explain how it all happened (this name is important).
Before we continue, it’s important to note that he claims that he was working with attorney generals in several states (see first video in this article). If true, it would mean that the routers used in the election should validate the data he presents in this video. Personally, I cannot confirm anything he’s claimed.
Who is Dennis Montgomery?
Now, we start getting into the strange part of the story. In Absolute Proof there are a number of people interviewed and evidence presented by Mike Lindell that is unrelated to hacking, but does paint a picture. Specifically, that the machines were connected to the internet and in some cases attorney’s were threatened with disbarment for assisting in court cases.
However, the key argument that Lindell makes are that “they” have data showing the elections were hacked. Mary Fanning was the women presenting the routing information (supposedly from the hacks) in Lindell’s video Absolute Proof. When searching “Mary Fanning“, it appears she is an author at theamericanreport.org.
The first article I happened across by her was regarding the Obama administration spying on the Trump campaign in 2016. When reviewing her body of work, I came across a name: “Dennis Montgomery“. That’s when I recalled reading an article from the Daily Beast: Infamous ‘Hoax’ Artist Behind Trumpworld’s New Voter Fraud Claim, in which the following was mentioned:
The election fraud claims center on Dennis Montgomery, a former intelligence contractor and self-proclaimed whistleblower who claims to have created the “Hammer” supercomputer and the “Scorecard” software some Trump fans believe was used to change the votes.
According to Mary Fanning’s reporting the Hammer is a supercomputer operating system developed by Dennis Montgomery. Dennis Montgomery is a whistle blower claiming that the U.S. government, particularly the NSA and FBI are spying domestically on American’s and effecting a coup. That particular story culminates in the release of Christopher Steele’s 2017 confession to the FBI.
Given Mary’s presentation and body of work, I believe the “data” in Absolute Proof is likely from Dennis Montgomery. However, it could be someone else as well.
A History of Dennis Montgomery
The history of Dennis Montgomery appears like something out of a spy novel. From Wikipedia:
In 1998, Montgomery co-founded eTreppid Technologies with partner Warren Trepp to develop video compression and noise filtering software for the gaming and casino industries. Montgomery and Trepp evolved their offerings for military applications and in 2004 won a no-bid contract with the United States Department of Defense. Following a dispute over software ownership, Montgomery was separated from eTreppid in 2006 and formed a new venture with billionaire backers Edra and Tim Blixseth.
It has been stated that Dennis Montgomery was also involved in the 2003 event where several planes grounded due to a “terror alert”, these were triggered by software supposedly developed by Montgomery. Unfortunately, the only source I could find on this was from Democracy Now! (heavily bias) and they are reporting it from a piece written in the magazine Playboy in late 2009. Supposedly, the software was a fraud, but I am unable to confirm any details (and later won a multi-million dollar defense contract).
That being noted, the next time Montgomery appears to make waves is is in 2015. Dennis Montgomery came up an interview between Montgomery’s business partner Tim Blixseth and law enforcement in Maricopa county Arizona. During the interviews between Sheriff Joe Arpaio and Tim Blixseth, Tim Blixseth claims to have information from Montgomery, effectively showing millions of Americans (lawyers, business, judges, politicians) being hacked:
The description of the “hack” is simply discovering passwords via a rainbow attack, then accessing personal, corporate and government accounts (00:12:30). The “Hammer” supercomputer was used to run the rainbow attacks. Once into a system, Montgomery would download all of the mainframe data from companies or personal data, etc.
Voter Record Database
What’s interesting is around the 00:15:12 timestamp, Blixeth discusses downloading the voter registration database in Florida. Blixeth then describes uploading a different set of data to the voter registration database.
A similar event was noted in the 2016 election in California (as reported by NBC):
WASHINGTON — In a little-noticed episode in 2016, an unusual number of voters in Riverside, California, complained that they were turned away at the polls during the primary because their voter registration information had been changed.
The Riverside County district attorney, Mike Hestrin, investigated and determined that the voter records of dozens of people had been tampered with by hackers. Hestrin said this week that federal officials confirmed his suspicions in a private conversation, saying the details were classified.
I noticed something similar happening in Michigan, particularly after the election. It could have been a re-canvas of some nature, but the given policy in Michigan required the ballots to be separated from envelops prior to a ballot being counted. This means, that even if the voter registration database was updated after the election, the votes would still count. This is what convinced me something fishy was afoot and several attorney’s I reached out to agreed.
Given the multiple reports, Blixeth appears to be making reasonable claims.
Canvasing would prove if the voter record database was accurate. This is also something the Department of Justice recently warned against, claiming it was voter intimidation to conduct a canvas during a post election audit (which would incur criminal penalties):
There have been reports, with respect to some of the post-2020 ballot examinations, of proposals to
contact individuals face to face to see whether the individuals were qualified voters who had
actually voted. (page 7 of the statement by DOJ)
Context: Edward Snowden
It’s also important to note the context here, in 2013 Edward Snowden leaked classified details on how the U.S. works with mobile carriers, tech companies and internet hubs to track the online presence of almost everyone online. For a detailed look at those events, I recommend the PBS documentary United States of Secrets. During the following hearings James Clapper claimed they did not “wittingly” spy on Americans.
This was inaccurate, as the NSA did collect all of American’s metadata, this enables the monitoring connections and potentially content.
NSA Spying Tools
In addition, since 2016 NSA tools have been leaking to the public. Many of these tools are targeted and gaining access to computers and accounts. That is part of the reason we are seeing a rise in ransomware attacks. It’s important to put this into context as Dennis Montgomery has previously worked as a contractor for the Department of Defense and there are claims he has worked at the CIA (and NSA?) in the recording. There are multiple interesting tools released, many of which mirror what was claimed in that audio clip. There are two I find most interesting:
EternalBlue – The tool exploits a vulnerability in the Windows Server Message Block, a transport protocol that allows Windows machines to communicate with each other and other devices for things like remote services and file and printer sharing. Attackers manipulate flaws in how SMB handles certain packets to remotely execute any code they want. Once they have that foothold into that initial target device, they can then fan out across a network.
The NSA had this exploit for years and it’s unclear when it was developed, and works on: Windows Vista, Windows 7, Windows 8.1, Windows 10, Windows Server 2008, Windows Server 2012, and Windows Server 2016.
Combined with CVE-2020-0688, described as
A remote code execution vulnerability exists in Microsoft Exchange software when the software fails to properly handle objects in memory, aka ‘Microsoft Exchange Memory Corruption Vulnerability’.
In reality, this enables an entire exchange server to be hijacked if a single user is compromised. It’s also important to note that this vulnerability was reported February 2020 and there are still many systems not updated.
Solar Winds
Finally, we get to Solar Winds — probably the largest hack in history. On December 8, 2020, FireEye (one of the worlds premier cybersecurity firms) announced it was hacked and their “Red Team” (i.e. hacking team’s) toolkit was stolen. On December 13, 2020, FireEye announced it was part of a supply chain attack, distributed through SolarWinds Orion software. Further, it was reported that the attack was initiated in March 2020.
This hack was massive and the hack appears to compromised much of the U.S. government, the Pentagon’s classified network was even shut down. In reality, given the level of compromise all the computer system(s) likely need to be rebuilt from scratch.
It is currently being claimed Russia was behind the hack. Personally, I am unconvinced, as I see no evidence — but that’s the narrative.
A side, but interesting note: SolarWinds Wi-Fi Packet Sniffer was the first result when searching for a WiFi packet capture program.
Dominion Voting Systems
One of the key arguments throughout the 2020 election audit debates has been around the voting machines.
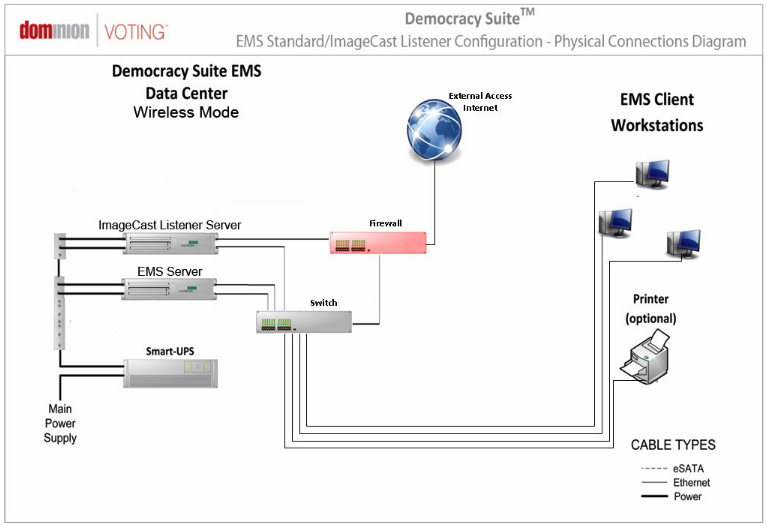
The Dominion Democracy Suite System is designed to be able to connect to the internet (Colorado Secretary of State Website) (austingwalters.com backup). That does not mean it was enabled.
The anti-virus software or operating system update on the Dominion Election Management System (EMS) in Maricopa County Arizona was not updated for at least 18 months (August 2019). Making them vulnerable to multiple forms of hacking.
At time of writing Maricopa County, is still refusing to release the routers to the Arizona Senate audit team to be inspected. Dominion systems is also not providing passwords to the county or state enabling system level access.
In Michigan, there were also multiple claims the machines were internet connected:
- Patrick Colbeck mapped out the network via the wiring (sorry, don’t like this website, but they cover it well)
- Barry Doherty described seeing roughly the same setup
Dominion Voting systems was using SolarWinds in 2020 (note, the logo was later removed).
Tying it Together
Why does this matter?
At the moment, we have the following pieces of data:
Dennis Montgomery
- Appears to have credentials in cyber security and data analysis
- Appears to have worked with the government (DOD, CIA)
- Has received no-bid tens-of-million dollar contracts from the DOD and has been financed by billionaires
- Claims he has the evidence & records of millions of Americans being hacked
- Claims that he can hack into peoples accounts (email, bank, etc)
- Unconfirmed history of providing faulty data
Mike Lindell
- Had / Has access to Trump
- Claims to have received election data in mid-January
- Presents evidence of every state being hacked
- Claims to have worked quietly with several state AGs to validate some of the data
- Hosts Mary Fanning on his show Absolute Proof (among many others)
- Invested tens of millions (as well as risks billion dollar lawsuits) in combating his perceived eleciton fraud
Cyber Security
- Microsoft Exchange Server zero-day exploit patched in Feb 2020
- SolarWinds compromised in March 2020 – June 2020
- (There were many other exploits in 2020)
Dominion Voting Systems
- Dominion Voting Systems EMS could be setup for internet access
- Multiple reports the Dominion Voting Systems in Michigan were setup for internet access
- Dominion Voting Systems appeared to use Solar Winds
- Dominion Voting Systems EMS (Election Management Software) was not up-to-date in Arizona
Legal
- Maricopa County Arizona is not providing their routers to the Arizona State Senate Auditors
- Dominion Voting Systems is not providing passwords to their machines to the Arizona State Senate Auditors
So, Where’s the Data?
On Aug 10 – 12, 2021, Mike Lindell is hosting a “Cyber Symposium” where the data will be accessible and where he’s invited tens of cyber experts and hundreds of politicians. He’s also offered five-million dollars if they anyone at the Symposium can prove the data is not real and from the 2020 election.
The only question I want answered, is where is the data from?
According to Lindell’s Absolute Proof video, they were using packet captures. Tying it back to the beginning packet captures occur by capturing the IP packets and analyzing the, often done by network administrators to assess security threats.
Which possibilities are most likely?
- voting machines or servers (central logging location)
- source routers
- antivirus software
- content delivery network (CDN)
- internet backbone(s)
- Verizon, AT&T or other network provider
Assuming the allegations are true, I see these as the most probable data sources:
- Someone working in an internet backbone, carriers or CDN thought it was a good idea to capture all packets
- Dennis Montgomery or some working group hacked into these locations and monitored the data
- Some agency hacked into SolarWinds and utilized passwords to obtain the access needed to conduct the sniffing
Assuming the packet captures are fake, I believe Dennis Montgomery and Mary Fanning to be the source to Mike Lindell. Though potentially, they received the data from someone else.
If true, the most likely scenario
Given the scale Mike Lindell is discussing (all 50 states) and claims they can see which votes were flipped (implying no TLS or access on the machines themselves) the most likely scenario is some sort of massive hack or multiple insiders. Hacking the voting machines or antivirus software via a supply chain hack (SolarWinds) or the MS Exchange hack(s) are the most likely scenarios in my mind.
There is a possibility of routers providing the information Lindell described, but there are only a few limited ways. For instance, the 2.02 Dominion Democracy Suite manual, they mention utilizing Microsoft SQL Sever 2012 for local “data centers” (i.e. on site). SQL Server 2012 does not have TLS enabled by default. I’m not sure what other vendors using today, I couldn’t find that documentation (and I assume much of it has been scrubbed).
SQL Server 2012 does not have TLS enabled by default. I’m not sure what other vendors using today, I couldn’t find that documentation (and I assume much of it has been scrubbed).
I also think the most likely scenario would be some sort of distributed code. It just does not seem likely that a team could hack into all of the various systems and locations, something would have to tie them all together.
Closing Thoughts
After writing this, I am amazed at how vulnerable and closed our voting systems are. Personally, I think we should image all the ballots and do hand counts. Then ensure the hand counts match the scanned ballots — that’s it. The hand count should be 3x people confirming the ballot says the same thing and move on. Which is basically what we had done for the prior 200 years in this country (until the 2000’s).
At the end of the day, I don’t think Mike Lindell’s data is legitimate. Although, I’m not sure that was the point. To confirm his claims, forensic audits and canvasing needs to be done. Which frankly, I think should be done every time to ensure a fair election. Especially, given the SolarWinds and MS Exchange hacks.
The fact is many in the United States don’t trust our election system and it is truly sad and infuriating. Lack of or feeling of representation was the basis for the revolutionary war. I for one, grew up near Chicago and everyone believed the elections were stolen — and I mean everyone: left, right and center. To be fair, Illinois and particularly Chicago is known to be corrupt.
My thoughts are simple: let anyone, anywhere inspect their local elections. Empower the populace to feel engaged and society will improve. Use the law to ensure a safe audit, but the people have a right to inspect their elections. Lindell has a right to make a fool of himself. Fighting the audits, only makes things significantly worse. Mocking those who believe the election was stolen will enrage them. Evaluating the ballots and bringing lawsuits is preferable to the alternatives.


A friend of mine worked for Dennis Montgomery around 2007. Tried to convince me to leave Microsoft and join the company. It sounded suspicious; making impossible sounding claims of the tech. I read Montgomery’s patents that were absolute garbage. Gave it a pass. Wasn’t long after the FBI were raiding the offices. Total grifter. I am amazed he is still grifting. Mike Lindell is an easy mark, I guess.
Will you be updating any of your analysis or assertions after Lindell’s symposium has concluded?
We don’t want to enrage those claiming fraud. They might break into the Capitol, attacks security, and go looking to hang the VP.
BTW, audits are no conducted by unqualified partisans with agendas. Why would anyone support that nonsense?